Quantum key distribution
Quantum cryptography is a technology arising from the broad field of quantum information which is more developed towards real world applications, with a few companies starting to offer commercial products.
Top | Implementation | Hardware | Software | Performance | E91 protocol | Daylight operation | Hacking | References
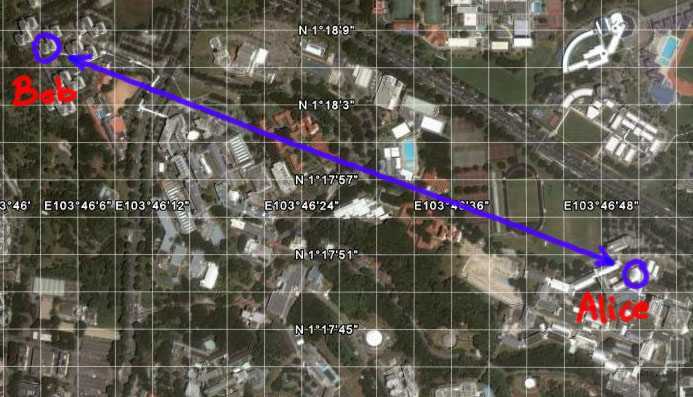
We implement a field version of free space quantum cryptography for
the urban environment of Singapore. A compact source of entangled
photon pairs is used to implement a
BB84-type quantum key distribution protocol. The system is able to
detect single photons in an outdoor
environment and against a strong background at moderate daylight
conditions. A
successful key exchange over a test range on NUS campus has been
demonstrated.
Implementation
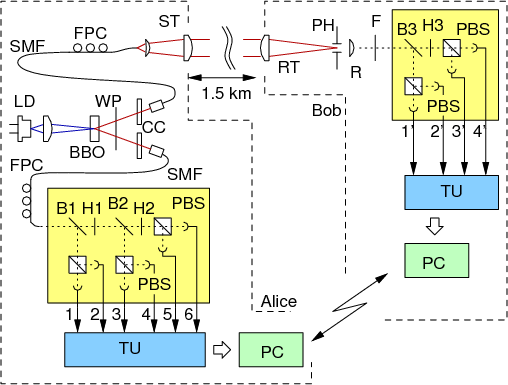
To explore key distribution systems relying on entangled photons as a primary physical resource for key generation, we follow currently a simple extension of a BB84 protocol, based on polarization measurements on photon pairs at two legitimate communication partners:
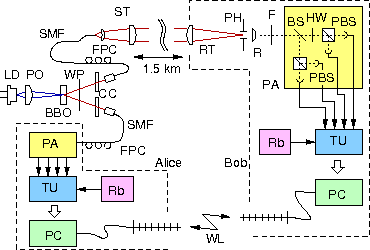
Besides
the source for entangled photon pairs, we use compact single photon
detection modules for polarization measurements, and a coincidence
identification concept with records times relative to local clocks on
both sides, obliviating any specific hardware communication channel for
the protocol besides the quantum link itself. After a few seconds of
our photon-pair based clock synchronization scheme, the key generation
process runs continuously using an autonomous standard WIFI link
between or two sides for all coincidence detection and genuine key
generation protocol elements such as base reconciliation, error
correction and privacy amplification.
Somewhat different from other QKD implementations, this scheme
requires
no large bandwidth supply for very random numbers in order not to
undermine the in-principle security promised by QKD, but only a very
moderate bandwidth for the classical protocol parts.
Top | Implementation | Hardware | Software | Performance | E91 protocol | Daylight operation | Hacking | References
Hardware
Our
intent is to provide a reference system for investigating the practical
feasibility and security of a quantum key distribution system which is
not bound to optical fibers, but is reasonably mobile and can be
deployed under ad-hoc conditions. This required development of quantum
optical equipment compatible with environmental conditions in tropical
Singapore.

Software / Protocol aspects
In an attempt to minimize the effort in expensive and sensitive physical hardware, we moved large parts of the key generation tasks into the software of our system. All coincidence identification key sifting and error correction components, which are essential part of every QKD approach were implemented in a way that key material is generated continuously once the quantum link is established between the two sites. Lossless compression schemes for classical communication operate close to the Shannon limit, allowing us to work with consumer-grade networking equipment. Privacy-amplified key accumulates in well-defined standard packets to be consumed by a key management system to to be used for encryption of data.
The code that drives our crypto implementation has migrated to a google code project. This is also an attempt to provide a basis of a security discussion on an implementation level rather than on the conceptual level only, making this part of a larger programme to assess realistic systems [6].
Top | Implementation | Hardware | Software | Performance | E91 protocol | Daylight operation | Hacking | References
Performance
In an
uninterrupted run of establishment of secret key over the span of a
night, we arrived at a key rate after error correction and privacy
amplification of 630 bits per second on average. Our initial raw key
error ratio is limited by the imperfect polarization correlations of
our entangled photon source at night (4..5% QBER), and by ambient light
contributions at daytime.
|
|
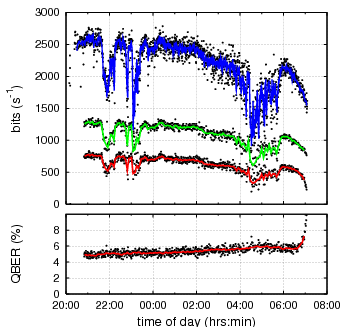
Key generation performance in a field trial over a run at
night. The blue trace shows the photon pair rate identified as
originating form the parametric down conversion source at the two
remote locations, subject to alignment drifts and atmospheric
transmission quality fluctuations. The green trace indicates our raw
key rate after basis reconciliation in a BB84-type protocol, and the
red trace the resulting final key rate after error correction and
privacy amplification, implementing a modified cascade error correction
protocol. The raw key error fraction (QBER, lower panel) is dominated by source correlations at night, and starts to see a sharp increase with the rising sun shining directly in the single photon detectors. |
Top | Implementation | Hardware | Software | Performance | E91 protocol | Daylight operation | Hacking | References
Implementation of an Ekert-91 protocol
One of the often quoted practical applications of entangled states are QKD
protocols which make explicit use of the monogamy of entanglement -
such that an eavesdropping attempt is revealed not via an error in the
established raw key, but in a reduction in the entanglement.
The violation of a Bell inequality can provide a quantitative measure for
this loss of entanglement, and an explicit assessment of the possible
knowledge of an eavesdropper was given in the framework of
device-independent cryptography [cite acin et al]. In the theoretical
scenario, this assessment makes no explicit assumption on the specific
measurement devices. In particular, it makes no assumption on the size of
the Hilbert space (and thus possible side channels).
We implemented a QKD protocol inspired by this idea, based on passive base
choices where we randomly either test for a violation of a CSHS Bell
inequality or generate a key.
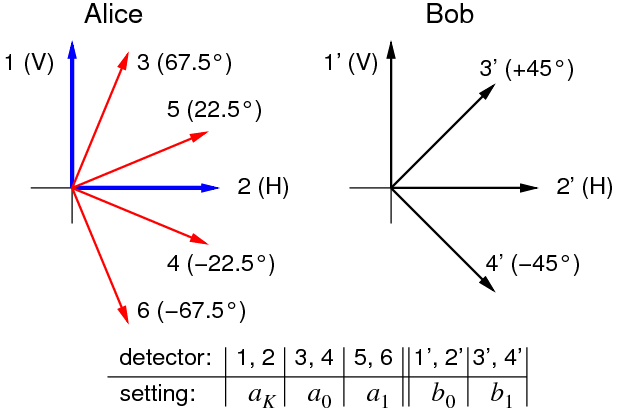 |
 |
We operated the key exchange based on this protocol over the same optical link on the NUS campus, and generate a secret key with an average Bell value of S=2.5 at a rate around 300 s-1. Technical details of that experimental implementation of the Ekert protocol can be found in [3].
Top | Implementation | Hardware | Software | Performance | E91 protocol | Daylight operation | Hacking | References
Daylight operation
Any free-space optical QKD link which claims some practical relevance needs to operate in daylight conditions. We succeeded to demonstrate this on campus with a BBM92 protocol, where our QKD system generated key without interruption over several days. The technical details can be found in [4]
Hacking
Any cryptography systems needs to prove its worthiness by being
subjected to attacks. We try to find explicit holes in the implementation and
explore the consequences of not addressing them.
Recently we looked into the
timing information exchanged between the communicating parties as a side
channel from which Eve can collect a large amount of information about the
key. See here or look up the
article [2] for a more details. Even more
recently we explored another, really large hole in the system (or comparable
ones) in collaboration with Vadim Makarov from
Trondheim/Norway[7]. More to come...
Varia
In December 2007 the full crypto kit was sent to Berlin to be demonstrated live at the Chaos Communication Congress. The kit survived the shipping, and the demo was a success. As part of the congress we also gave a talk and released the software and some test data that drives the QKD system as open source.
In the framework of the master thesis of Caleb Ho, an algorithm was developed to carry out the clock synchronization for the remote coincidence identification with relatively cheap clocks instead of Rubidium references or GPS receivers by exploiting the high temporal correlation of downconverted photon pairs only, thus reducing significantly the hardware requirements. See reference [5] for details.
Top | Implementation | Hardware | Software | Performance | E91 protocol | Daylight operation | Hacking | References
References
| [1] | I. Marcikic, A. Lamas-Linares, C. Kurtsiefer: Free-space quantum key distribution with entangled photons. Applied Physics Letters 89, 101122 (2006) |
| [2] | A. Lamas-Linares and C.Kurtsiefer: Breaking a quantum key distribution system through a timing side channel. Opt. Express 15, 9388 (2007) |
| [3] | A. Ling, M.P. Peloso, I. Marcikic, V. Scarani, A.Lamas-Linares, C. Kurtsiefer: Experimental quantum key distribution based on a Bell test. Physical Review A 78, 020301 (R) (2008) |
| [4] | M.P. Peloso, I. Gerhardt, C. Ho, A. Lamas-Linares, C. Kurtsiefer: Daylight operation of a free space, entanglement-based quantum key distribution system. New Journal of Physics 11, 045007 (2009) |
| [5] | C.Ho, A. Lamas-Linares, C. Kurtsiefer: Clock synchronization by remote detection of correlated photon pairs. New Journal of Physics 11, 045011 (2009) |
| [6] | V. Scarani, C. Kurtsiefer: The black paper of quantum cryptography: real implementation problems. arXiv:0906.4547 (2009) |
| [7] | I. Gerhardt, Q. Liu, A. Lamas-Linares, J. Skaar, C. Kurtsiefer, V. Makarov: Full-field implementation of a perfect eavesdropper on a quantum cryptography system, Nature communications 2, 349 (2011) / arXiv:1011.0105 (2010) |